2016 June Microsoft Official: 70-697 PDF Dumps & 70-697 VCE Dumps with New 70-697 Exam Questions Released Today by Braindump2go.com! 100% Exam Pass Guaranteed!
NEW QUESTION 51 – NEW QUESTION 60:
QUESTION 51
Hotspot Question
You have a network that contains Window 10 Enterprise computers.
The network configuration of one of the computers is shown in the following output.

Use the drop-down menus to select the answer choice that completes each statement based on the information presented in the output.
NOTE: Each correct selection is worth one point.

Answer:

Explanation:
The exhibit below shows that the computer obtained its IPv4 address from a DHCP server. It also shows when the DHCP lease was obtained and when it will expire.
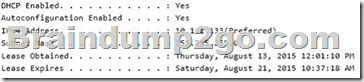
The IPv6 address shown below starts with `fe80′. This is an auto-configuration address, not an address obtained from a DHCP server.

The IP address of the Default Gateway is 10.1.1.1
QUESTION 52
Hotspot Question
You are setting up a Windows 10 Enterprise computer.
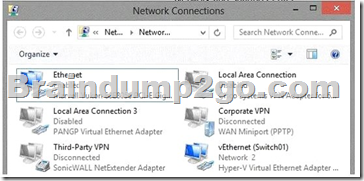
The computer’s network connections are shown in the Network connections exhibit. (Click the Exhibit button.)
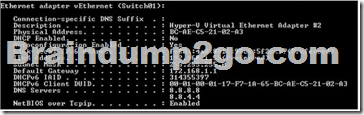
The computer’s network settings are shown in the Network Settings exhibit. (Click the Exhibit button.)
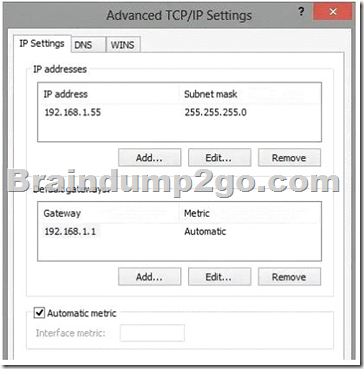
Advanced TCP/IP settings are shown in the Advanced TCP/IP Settings exhibit. (Click the Exhibit button.)
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
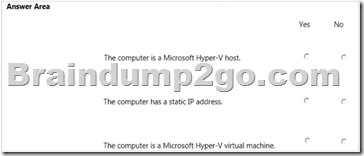
Answer:
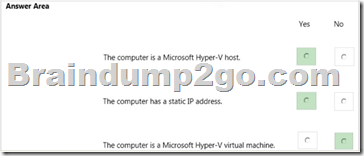
Explanation:
The computer has a physical network adapter.
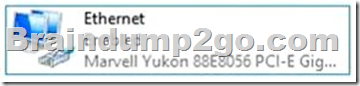
When you enable Hyper-V on a computer, a virtual network adapter connected to a virtual switch is added.
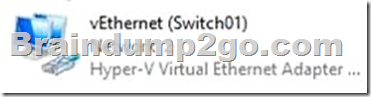
Therefore, the computer is a Hyper-V host.
The computer has an IP address. The text in the image below shows that the network connection is not DHCP enabled. Therefore, this is a static IP address.

The computer is a Hyper-V host, not a Hyper-V virtual machine.
QUESTION 53
A company has client computers that run Windows 10.
The client computer systems frequently use IPSec tunnels to securely transmit data.
You need to configure the IPSec tunnels to use 256-bit encryption keys.
Which encryption type should you use?
A. 3DES
B. DES
C. RSA
D. AES
Answer: D
QUESTION 54
You administer a group of 10 client computers that run Windows 10.
The client computers are members of a local workgroup.
Employees log on to the client computers by using their Microsoft accounts.
The company plans to use Windows BitLocker Drive Encryption.
You need to back up the BitLocker recovery key.
Which two options can you use? (Each correct answer presents a complete solution. Choose two.)
A. Save the recovery key to a file on the BitLocker-encrypted drive.
B. Save the recovery key in the Credential Store.
C. Save the recovery key to SkyDrive.
D. Print the recovery key.
Answer: CD
Explanation:
It’s not possible to save a Bitlocker file into the same disk. Moreover, what would be the point to save recovery key on the drive, which is locked and you cannot access it without the key anyway.
QUESTION 55
You are using sysprep to prepare a system for imaging.
You want to reset the security ID (SID) and clear the event logs.
Which option should you use?
A. /generalize
B. /oobe
C. /audit
D. /unattend
Answer: A
Explanation:
Generalize prepares the Windows installation to be imaged.
If this option is specified, all unique system information is removed from the Windows installation. The security ID (SID) resets, any system restore points are cleared, and event logs are deleted.
The next time the computer starts, the specialize configuration pass runs. A new security ID (SID) is created, and the clock for Windows activation resets, if the clock has not already been reset three times.
QUESTION 56
Group Policy is a set of rules which control the working environment of user accounts and computer accounts. Group Policy provides the centralized management and configuration of operating systems, applications and users’ settings in an Active Directory environment.
In other words, Group Policy in part controls what users can and can’t do on a computer system.
Which one of these policies requires a reboot?
A. Turn off Windows Defender
B. Turn off Autoplay for non-volume devices
C. Disable Active Desktop
D. Turn off Data Execution Prevention for Explorer
Answer: D
Explanation:
You can Turn Off Windows Defender anytime (Uninstalling it is another thing!) without rebooting.
A reboot is REQUIRED when turning off DEP for Explorer.
QUESTION 57
Which term is used to refer to installing apps directly to a device without going through the Windows Store?
A. SQL Injection
B. BranchCache
C. DLL Hijack
D. Sideloading
Answer: D
QUESTION 58
IPv6 has a vastly larger address space than IPv4.
This expansion provides flexibility in allocating addresses and routing traffic and eliminates the primary need for network address translation (NAT).
Do you know how many more bits there are in an IPv4 address compared to an IPv6 address?
A. 4 times more
B. 6 times more
C. Twice as many
D. 8 times more
Answer: A
Explanation:
IPv4 addresses are 32 bit, IPv6 addresses are 128 bit.
QUESTION 59
You are using sysprep to prepare a system for imaging.
You want to enable end users to customize their Windows operating system, create user accounts, name the computer, and other tasks.
Which sysprep setting should you use?
A. /oobe
B. /audit
C. /generalize
D. /unattend
Answer: A
QUESTION 60
You have set up a new wireless network for one of your prestigious clients.
The director wants to ensure that only certain designated wireless laptops can connect to the new network to prevent misuse.
What do you need to do?
A. Use MAC address control
B. Use IPv4 address control
C. Use WEP
D. Use WPA
Answer: A
Explanation:
Media Access Control address (MAC address) is a unique identifier assigned to most network adapters or network interface cards (NICs) by the manufacturer for identification, and used in the Media Access Control protocol sub-layer. If assigned by the manufacturer, a MAC address usually encodes the manufacturer’s registered identification number. It may also be known as an Ethernet Hardware Address (EHA), hardware address, adapter address, or physical address.
2016 Valid Microsoft 70-697 Study Materials:
1.| Latest 70-697 PDF & 70-697 VCE 84Q&As from Braindump2go: http://www.braindump2go.com/70-697.html[100% [Exam Pass Guaranteed!]
2.| New 70-697 Exam Questions and Answers – Google Drive: https://drive.google.com/folderview?id=0B75b5xYLjSSNMHZoZGJxbElJbFU&usp=sharing