2018/November Braindump2go 70-744 Exam Dumps with PDF and VCE New Updated Today! Following are some new 70-744 Real Exam Questions:
1.|2018 Latest 70-744 Exam Dumps (PDF & VCE) 201Q&As Download:
https://www.braindump2go.com/70-744.html
2.|2018 Latest 70-744 Exam Questions & Answers Download:
https://drive.google.com/drive/folders/0B75b5xYLjSSNMDN6VjRLbFVKaWM?usp=sharing
QUESTION 102
Your network contains an Active Directory domain named contoso.com.
The domain contains a member server named Servers that runs Windows Server 2016.
You need to configure Servers as a Just Enough Administration (JEA) endpoint.
Which two actions should you perform? Each correct answer presents part of the solution.
A. Create and export a Windows PowerShell session.
B. Deploy Microsoft Identity Manager (MIM) 2016
C. Create a maintenance Role Capability file
D. Generate a random Globally Unique Identifier (GUID)
E. Create and register a session configuration file.
Answer: CE
Explanation:
https://docs.microsoft.com/en-us/powershell/jea/role-capabilities
https://docs.microsoft.com/en-us/powershell/jea/register-jea
QUESTION 103
You have a server named Server1 that runs Windows Server 2016.
You configure Just Enough Administration (JEA) on Server1.
You need to view a list of commands that will be available to a user named User1 when User1 establishes a JEA session to Server1.
Which cmdlet should you use?
A. Trace-Command
B. Get-PSSessionCapability
C. Get-PSSessionConfiguration
D. Show-Command
Answer: B
Explanation:
The Get-PSSessionCapability cmdlet gets the capabilities of a specific user on a constrained sessionconfiguration.Use this cmdlet to audit customized session configurations for users.Starting in Windows PowerShell 5.0, you can use the RoleDefinitions property in a session configuration (.pssc)file.Using this property lets you grant users different capabilities on a single constrained endpoint based on groupmembership.The Get-PSSessionCapability cmdlet reduces complexity when auditing these endpoints by letting youdetermine the exact capabilities granted to a user.This command is used by I.T. Administrator (The “You” mention in the question) to verify configuration for aUser.
QUESTION 104
You have a file server named Server1 that runs Windows Server 2016.
A new policy states that ZIP files must not be stored on Server1.
An administrator creates a file screen filter as shown in the following output
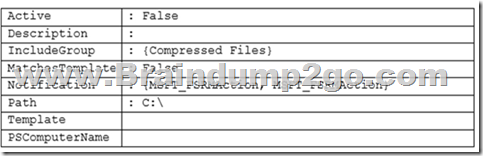
You need to prevent users from storing ZIP files on Server1, what should you do?
A. Enable Quota Management on all the drives.
B. Add a template to the filter.
C. Change the filter to active.
D. Configure File System (Global Object Access Auditing).
Answer: C
Explanation:
“Active : False”, then it is a Passive Filescreen filther which will not block unwanted file types.
QUESTION 105
Your network contains an Active Directory forest named contoso.com.
The forest functional level is Windows Server 2012.
The forest contains 20 member servers that are configured as file servers.
All domain controllers run Windows Server 2016.
You create a new forest named contosoadmin.com.
You need to use the Enhanced Security Administrative Environment (ESAE) approach for the administration of the resources in contoso.com.
Which two actions should you perform? Each correct answer presents part of the solution.
A. From the properties of the trust, enable selective authentication.
B. Configure contosoadmin.com to trust contoso.com.
C. Configure contoso.com to trust contosoadmin.com.
D. From the properties of the trust, enable forest-wide authentication.
E. Configure a two-way trust between both forests.
Answer: AC
QUESTION 106
Your network contains an Active Directory domain named contoso.com.
The domain contains a server named Server1 that runs Windows Server 2016.
You need to prevent NTLM authentication on Server1.
Solution: From Windows PowerShell, you run the Disable-WindowsOptionalFeature cmdlet.
Does this meet the goal?
A. Yes
B. No
Answer: B
Explanation:
https://blogs.technet.microsoft.com/filecab/2016/09/16/stop-using-smb1/
On Client, the PowerShell approach (Disable-WindowsOptionalFeature -Online -FeatureName smb1protocol)Disable-WindowsOptionalFeature -Online -FeatureName smb1protocol
However, the question asks about Server!On Server, the PowerShell approach (Remove- WindowsFeature FS-SMB1):Remove-WindowsFeature FS-SMB1
Even if SMB1 is removed, SMB2 and SMB3 could still run NTLM authentication! Therefore, answer is a”NO”.
QUESTION 107
Your network contains an Active Directory domain named contoso.com.
The domain contains a computer named Computer1 that runs Windows 10.
The network uses the 172.16.0.0/16 address space.
Computer1 has an application named App1.exe that is located in D:\\Apps\\.
App1.exe is configured to accept connections on TCP port 8080.
You need to ensure that App1.exe can accept connections only when Computer1 is connected to the corporate network.
Solution: You configure an inbound rule that allows the TCP protocol on port 8080 and applies to all profiles.
Does this meet the goal?
A. Yes
B. No
Answer: B
Explanation:
You need to ensure that App1.exe can accept connections only when Computer1 is connected to the corporatenetwork.
Therefore, you should not create firewall rule for all three profiles.
QUESTION 108
You have a guarded fabric and a Host Guardian Service server named HGS1.
You deploy a Hyper-V host named Hyper1, and configure Hyper1 as part of the guarded fabric.
You plan to deploy the first shielded virtual machine.
You need to ensure that you can run the virtual machine on Hyper1.
What should you do?
A. On Hyper1, run the Invoke-WebRequest cmdlet, and then run the Import-HgsGuardian cmdlet.
B. On HGS1, run the Invoke-WebRequest cmdlet, and then run the Import-HgsGuardian cmdlet.
C. On Hyper1, run the Export-HgsKeyProtectionState cmdlet, and then run the Import- HgsGuardian cmdlet.
D. On HGS1, run the Export-HgsKeyProtectionState cmdlet, and then run the Import- HgsGuardian cmdlet
Answer: A
Explanation:
https://blogs.technet.microsoft.com/datacentersecurity/2016/06/06/step-by-step-creating-shielded-vms-withoutvmm/
QUESTION 109
Your network contains an Active Directory domain named contoso.com.
All servers in the domain run Windows Server 2016.All client computers run Windows 10.
Your company has deployed the Local Administrator Password Solution (LAPS).
Client computers in the finance department are located in an organizational unit (OU) named Finance.
Each finance computer has a custom administrative account named FinAdmin.
You discover that the FinAdmin accounts are not managed by LAPS.
You need to ensure that the FinAdmin accounts are managed by LAPS. What should you do?
A. On the finance computers, register the AdmPwd.ps Windows PowerShell module and then run the ResetAdmPwdPassword cmdlet
B. Modify the Password Policy in a Group Policy object (GPO).
C. Modify the LAPS settings in a Group Policy object (GPO).
D. On the finance computers. rename the FinAdmin accounts to Administrator.
Answer: C
Explanation:
Use the GPO Setting “Name of administrator account to manage” for LAPS to manage secondaryadministrative accounts which is not named as “Administrator”
QUESTION 110
Your network contains an Active Directory domain named contoso.com.
The domain contains a server named
Server1 that runs Windows Server 2016.
You have an organizational unit (OU) named Administration that contains the computer account of Server1.
You import the Active Directory module to Server1.
You create a Group Policy object (GPO) named GPO1. You link GPO1 to the Administration OU.
You need to log an event each time an Active Directory cmdlet executed successfully from Server1.
What should you do?
A. From Advanced Audit Policy in GPO1. configure auditing for other privilege use events.
B. Run the Add-NetEventProvider -Name “Microsoft-Active-Directory” -MatchAnyKeyword PowerShell command.
C. From Advanced Audit Policy in GPO1, configure auditing for directory service changes.
D. From Administrative Templates in GPO1, configure a Windows PowerShell policy.
Answer: D
Explanation:
In the following GPO location, you can enable the setting “Turn on Module Logging” to record an event eachtime the PowerShell executes a cmdlet of a specificPowerShell module, for example “ActiveDirectory”.”Computer Configuration\\Administrative Templates\\Windows Components\\Windows PowerShell”
QUESTION 111
Your network contains an Active Directory domain named contoso.com.
The domain contains several shielded virtual machines.
You deploy a new server named Server1 that runs Windows Server 2016.
You install the Hyper-V server role on Server1.
You need to ensure that you can host shielded virtual machines on Server1.
What should you install on Server1?
A. Host Guardian Hyper-V Support
B. BitLocker Network Unlock
C. the Windows Biometric Framework (WBF)
D. VM Shielding Tools for Fabric Management
Answer: A
Explanation:
This questions mentions “The domain contains several shielded virtual machines.”, which indicates a workingHost Guardian Service deployment was completed.
https://docs.microsoft.com/en-us/windows-server/virtualization/guarded-fabric-shielded-vm/guarded-fabricguarded-host-prerequisites
For a new Hyper-V server to utilize an existing Host Guardian Service, install the “Host Guardian Hyper-VSupport”.
QUESTION 112
You network contains an Active Directory forest named contoso.com.
All domain controllers run Windows Server 2016 Member servers run either Windows Server 2012 R2 or Windows Server 2016.
Client computers run either Windows 8.1 or Windows 10.
You need to ensure that when users access files in shared folders on the network, the files are encrypted when they are transferred over the network.
Solution: You enable SMB encryption on all the computers in domain.
Does this meet the goal?
A. Yes
B. No
Answer: A
Explanation:
SMB Encryption could be enabled on a per-computer wide basis, after you have enabled SMB encryption on aserver-level basis, you could not disable encryptionfor any specific shared folder.
To enable Global level encryption on the server:Set- SmbServerConfiguration -EncryptData 1
!!!RECOMMEND!!!
1.|2018 Latest 70-744 Exam Dumps (PDF & VCE) 201Q&As Download:
https://www.braindump2go.com/70-744.html
2.|2018 Latest 70-744 Study Guide Video: